Page 63 - IRMSA Risk Report 2020
P. 63
EXPERT OPINION
ROSS FORGAN
DIREC TOR, NORTON ROSE FULBRIGHT
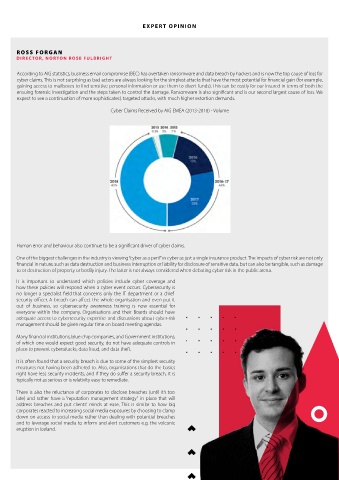
According to AIG statistics, business email compromise (BEC) has overtaken ransomware and data breach by hackers and is now the top cause of loss for
cyber claims. This is not surprising as bad actors are always looking for the simplest attacks that have the most potential for financial gain (for example,
gaining access to mailboxes to find sensitive personal information or use them to divert funds). This can be costly for our insured in terms of both the
ensuing forensic investigation and the steps taken to control the damage. Ransomware is also significant and is our second largest cause of loss. We
expect to see a continuation of more sophisticated, targeted attacks, with much higher extortion demands.
Cyber Claims Received by AIG EMEA (2013-2018) - Volume
Human error and behaviour also continue to be a significant driver of cyber claims.
One of the biggest challenges in the industry is viewing “cyber as a peril” vs cyber as just a single insurance product. The impacts of cyber risk are not only
financial in nature, such as data destruction and business interruption or liability for disclosure of sensitive data, but can also be tangible, such as damage
to or destruction of property or bodily injury. The latter is not always considered when debating cyber risk in the public arena.
It is important to understand which policies include cyber coverage and
how these policies will respond when a cyber event occurs. Cybersecurity is
no longer a specialist field that concerns only the IT department or a chief
security officer. A breach can affect the whole organisation and even put it
out of business, so cybersecurity awareness training is now essential for
everyone within the company. Organisations and their Boards should have
adequate access to cybersecurity expertise and discussions about cyber-risk
management should be given regular time on board meeting agendas.
Many financial institutions, blue chip companies, and Government institutions,
of which one would expect good security, do not have adequate controls in
place to prevent cyberattacks, data fraud, and data theft.
It is often found that a security breach is due to some of the simplest security
measures not having been adhered to. Also, organisations that do the basics
right have less security incidents, and if they do suffer a security breach, it is
typically not as serious or is relativity easy to remediate.
There is also the reluctance of corporates to disclose breaches (until it’s too
late) and rather have a “reputation management strategy” in place that will
address breaches and put clients’ minds at ease. This is similar to how big
corporates reacted to increasing social media exposures by choosing to clamp
down on access to social media rather than dealing with potential breaches
and to leverage social media to inform and alert customers e.g. the volcanic
eruption in Iceland.