Page 62 - IRMSA Risk Report 2020
P. 62
4.3.11
C Y BER AT TA CKS , D ATA FR A UD AND D ATA THEFT
DUE TO INCREASING TECHNOLOGY ADVANCES AND COMPLEXITIES, CYBERCRIME MAY ESCALATE BEYOND
ORGANISATIONS’ CAPABILITY TO MANAGE, IMPACTING ON INDIVIDUAL ORGANISATION’S ABILITY TO OPERATE,
AND OVERALL ECONOMIC GROWTH AND BUSINESS CONFIDENCE.
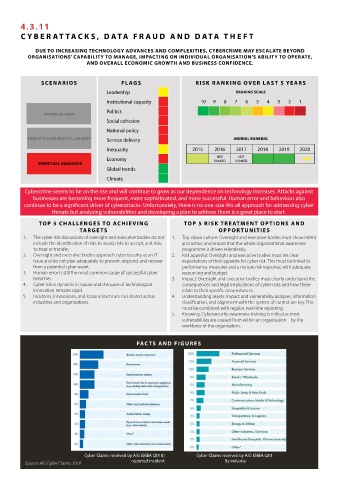
SCENARIOS FLAGS RISK RANKING OVER LAST 5 YEARS
Leadership RANKING SCALE
Institutional capacity 10 9 8 7 6 5 4 3 2 1
Politics
SPRING OF HOPE
Social cohesion
National policy
FAKE IT TILL WE MAKE IT...OR NOT? Service delivery ANNUAL RANKING
Inequality 2015 2016 2017 2018 2019 2020
NOT
NOT
Economy RANKED RANKED
PERPETUAL HANGOVER
Global trends
Climate
Cybercrime seems to be on the rise and will continue to grow as our dependence on technology increases. Attacks against
businesses are becoming more frequent, more sophisticated, and more successful. Human error and behaviour also
continue to be a significant driver of cyberattacks. Unfortunately, there is no one-size-fits-all approach for addressing cyber
threats but analysing vulnerabilities and developing a plan to address them is a great place to start.
TOP 5 CHALLENGES TO ACHIEVING TOP 5 RISK TREATMENT OPTIONS AND
TARGETS OPPORTUNITIES
1. The cyber risk discussions of oversight and executive bodies do not 1. Top-down culture: Oversight and executive bodies must show intent
include the identification of risks to avoid, risks to accept, and risks and action and ensure that the whole organisational awareness
to treat or transfer. programme is driven relentlessly.
2. Oversight and executive bodies approach cybersecurity as an IT 2. Risk appetite: Oversight and executive bodies must set clear
issue and do not plan adequately to prevent, respond, and recover expectations of their appetite for cyber risk. This must be linked to
from a potential cyber event. performance measures and a mature risk response, with adequate
3. Human error is still the most common cause of successful cyber resourcing and budget.
breaches. 3. Impact: Oversight and executive bodies must clearly understand the
4. Cyber risk is dynamic in nature and the pace of technological consequences and legal implications of cyber risks and how these
innovation remains rapid. relate to their specific circumstances.
5. Incidents, innovations, and lessons learnt are not shared across 4. Understanding assets: Impact and vulnerability analyses, information
industries and organisations. classification, and alignment with the system of control are key. This
must be combined with regular, real-time reporting.
5. Knowing: Cybersecurity awareness training is critical as most
vulnerabilities are caused from within an organisation – by the
workforce of the organisation.
FAC TS AND FIGURES
Cyber Claims received by AIG EMEA (2018) Cyber Claims received by AIG EMEA (201
Source: AIG Cyber Claims 2019 reported incident By industry